A developer meticulously reverse-engineered Uber Eats and DoorDash, scraping 880K+ restaurants and 48M menu items into a searchable SQLite database to overcome the apps' weak keyword and price-sorting features. Exposing pricing bugs, rating quirks, and internal ranking secrets, Chowline doubles as a research tool for devs interested in API scraping, GraphQL, and Cloudflare evasion. This project highlights how food delivery giants have built a goldmine of structured data ripe for tech-driven inno
Reverse Engineering Uber Eats and DoorDash APIs to Build Chowline: 48M Menu Items for Smarter Food Searches
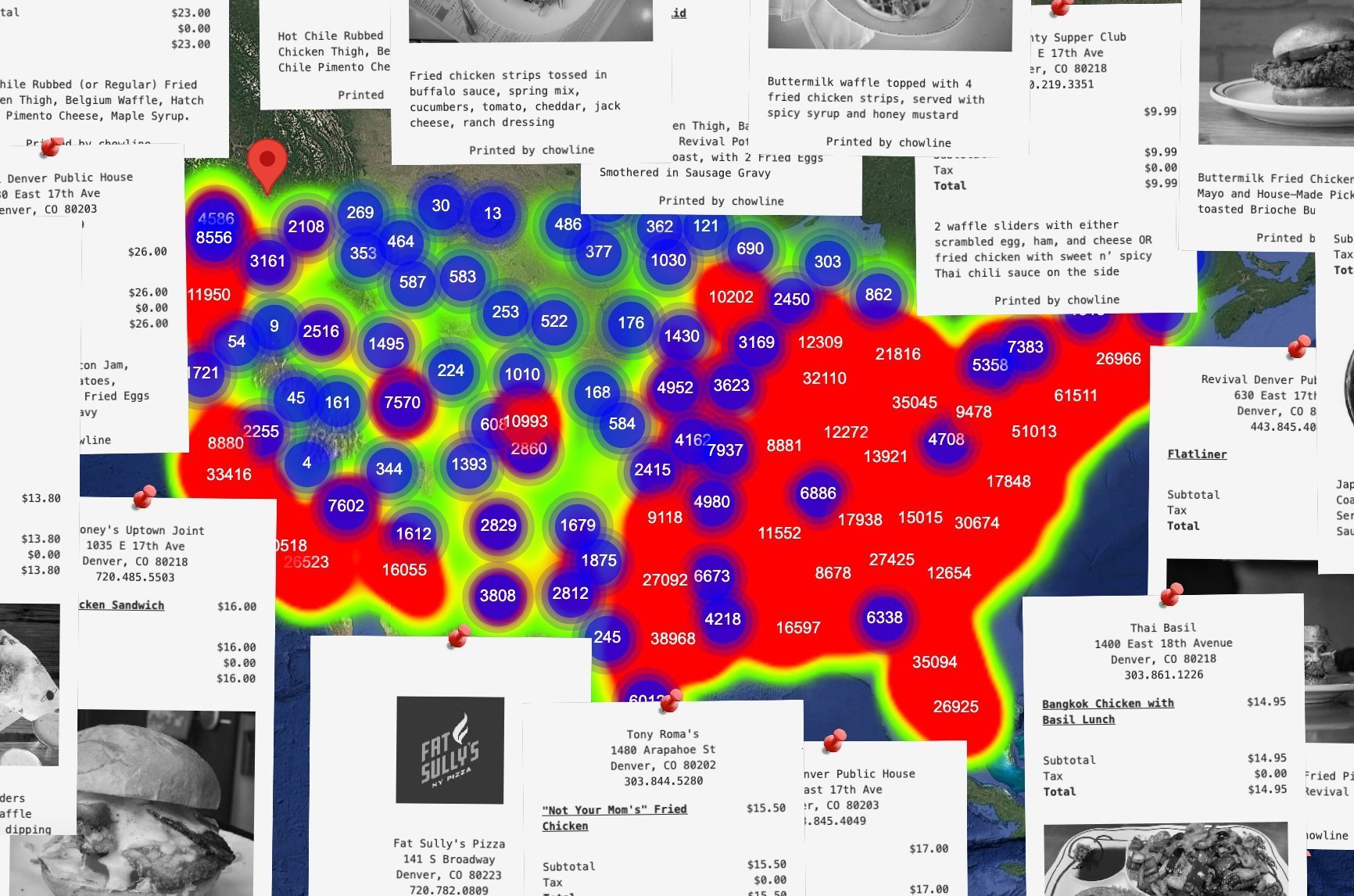
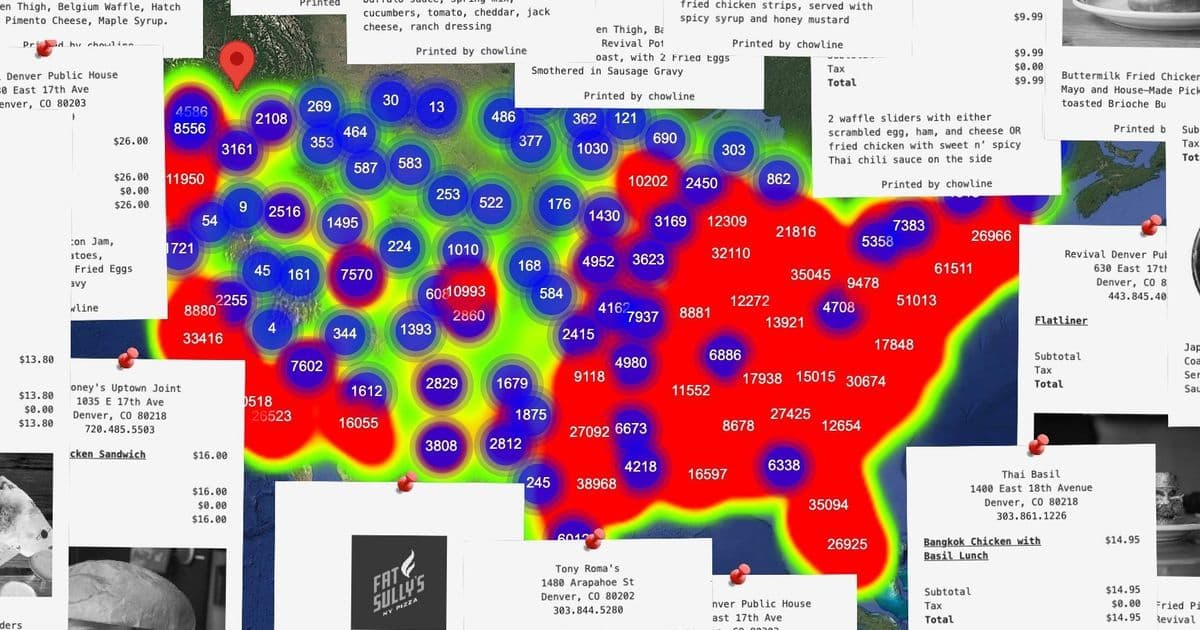
Food delivery apps like Uber Eats and DoorDash dominate the U.S. market, but their search limitations—no direct keyword matching on menus, no price sorting—frustrate users hunting specific dishes or deals. Enter Chowline: a reverse engineering project that scraped over 880,000 restaurants and 48 million menu items, storing them in a relational SQLite database for fast, flexible queries. Developer tgrcode, motivated by the 'burrito taxi' meme and hackathon demos, turned API inspection into a tool that outperforms the originals, while uncovering pricing glitches and operational insights.
Targeting Uber Eats: JSON Endpoints and Feed Scraping
Uber Eats proved the easier mark, with client-server interactions exposing clean JSON via POST requests. Setting a delivery location triggers /upsertDeliveryLocationV2 and /setTargetLocationV1, storing address data in the uev2.loc cookie. The homepage feed then loads via /getFeedV1, returning up to 500 results in a payload rich with store details.
The rating is interesting as the service bothers to give us an exceptionally precise double but does not give us a precise number of ratings, only a rough magnitude. score gives us some insight on how UberEats is ranking restaurants internally... UberEats appears to be using a Tobii T120 eye tracker in some isolated 'Human-in-the-Loop' approach.
This internal score field hints at hybrid recommendation systems blending graph neural networks with eye-tracking data from human testers. Paging requires pageInfo offsets and headers like x-csrf-token, Accept-Language, and Content-Type to avoid empty responses.
Store deep-dives via /getStoreV1 reveal menus nested in sections/subsections, complete with prices, ratings, images, and availability. Customizations were skipped due to per-item API calls, but core data sufficed for the 40GB dataset.
{
"type": "REGULAR_STORE",
"store": {
"id": "--nm23s0W5uMaIH978z80Q",
"name": "Runza Loveland CO",
"score": 4.2,
"lat": 40.405,
"lng": -105.076
}
}
Challenges like non-proximity-sorted results and delivery radius variances forced a 'random drone' scraping strategy over systematic coverage, ideal for hackathon speed.
Conquering DoorDash: GraphQL, Cloudflare, and uTLS
DoorDash, holding the largest U.S. share, relied on server-side rendered HTML and Cloudflare bot protection. Network tracing revealed GraphQL endpoints like pickupMapPage and storepageFeed, discovered partly via GitHub repo searches for /graphql/ patterns.
Cloudflare's __cf_bm checks were bypassed using Golang's uTLS for Firefox TLS fingerprinting, HTTP/2, and headers including Apollographql-Client-Name:
req.Header.Set("User-Agent", "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/121.0")
req.Header.Set("Apollographql-Client-Name", "doordash-graphql");
// uTLS: client, err := uTLS.NewClient(conn, &uTLS.ClientHelloSpec{Fingerprint: uTLS.Firefox_121}, nil)
Rate limits hit despite proxies, but standard user agents eventually worked. Common fields—store name, lat/lng, rating, price, availability—normalized into SQL tables alongside sections/subsections.
Data Goldmine: Anomalies and Research Potential
Chowline's frontend sorts by price, proximity, or rating, enabling queries like 'chicken tikka masala' in Denver, surfacing surprises such as a $12 cheesesteak variant. U.S. restaurants skew generous in ratings (mean 3.584, median 4.447) versus Japan's stingier 3.175 mean.
Pricing bugs exposed guardrails:
- Pre-July 2025: Negative prices enabled ~$6,000 free food exploits via offsets; now
RuleNegativeFareblocks. - Upper bounds: ~$10,000/item (
RuleUpperBound), with cart caps like $150/store. - Errors: Subway listings inflated by 1,000x.
This national food delivery dataset contains >880 thousand restaurants and >48 million menu items... Performing keyword searches on a 40 million menu item dataset does make it easier to find what I’m looking for.
Delivery fees were omitted due to per-location computation costs, shifting focus to research: discovering niche flavors like wintermelon milk tea amid vector-search shortcomings in official apps.
Lessons for Reverse Engineers and Devs
This saga showcases pragmatic API hunting—cookie tracking, CSRF handling, GraphQL probing—while navigating ToS gray areas. For developers, it demonstrates how platforms aggregate structured data (menus as JSON/GraphQL) for unintended reuse, fueling tools like Chowline. As food apps evolve with patches, such projects remind us that reverse engineering not only solves user pains but illuminates the fragile logic powering everyday services.
Source: Digging Into Food Delivery With Chowline, by tgrcode, November 25, 2025.
Comments
Please log in or register to join the discussion