A critical authentication bypass in SmarterMail's password reset endpoint was actively exploited just 48 hours after the vendor released a patch, highlighting the risks of vague security advisories and the speed at which attackers reverse-engineer fixes.
A critical authentication bypass vulnerability in SmarterTools' SmarterMail email server software was actively exploited in the wild just two days after the company released a patch. The flaw, tracked by watchTowr Labs as WT-2026-0001, allows an attacker to reset the system administrator password via a simple HTTP request, granting them immediate remote code execution (RCE) capabilities on the underlying server.
The vulnerability resides in the SmarterMail.Web.Api.AuthenticationController.ForceResetPassword function, which handles password reset requests. According to watchTowr Labs researchers Piotr Bazydlo and Sina Kheirkhah, the endpoint was reachable without any authentication. The core of the issue lies in a boolean flag named IsSysAdmin that the endpoint uses to determine the type of user requesting the reset.
When an attacker sends a crafted request to /api/v1/auth/force-reset-password with the IsSysAdmin flag set to true and provides a valid administrator username, the system performs a dangerous sequence of actions:
- It retrieves the configuration for the specified username.
- It creates a new system administrator item with the attacker's chosen password.
- It updates the original administrator account with this new password.
This complete lack of security control means anyone with knowledge of an existing administrator username can instantly take over the account. Once they have admin access, the path to full server compromise is straightforward. SmarterMail includes a built-in feature allowing system administrators to execute operating system commands by creating a new volume and supplying an arbitrary command in the "Volume Mount Command" field. This command runs with SYSTEM-level privileges, giving the attacker a shell on the host machine.
SmarterTools patched the vulnerability on January 15, 2026, with Build 9511, following responsible disclosure from watchTowr Labs on January 8. However, the exploitation began on January 17, just 48 hours later. The incident came to light after a user on the SmarterTools Community Portal reported losing access to their admin account, with logs showing the force-reset-password endpoint was used to change the password. This suggests attackers quickly reverse-engineered the patch to understand and exploit the underlying flaw.
Compounding the problem was SmarterTools' release notes for Build 9511, which were notably vague. The notes simply listed "IMPORTANT: Critical security fixes" without specifying the nature of the vulnerabilities. This lack of transparency makes it difficult for administrators to assess the urgency of the update and understand what to look for in their logs.
In response to criticism, SmarterTools CEO Tim Uzzanti explained the company's historical practice. "In our 23+ years, we have had only a few CVEs, which were primarily communicated through release notes and critical fix references," Uzzanti stated. He acknowledged customer feedback and indicated a policy change moving forward, where the company plans to send email notifications for new CVEs and subsequent patches. It remains unclear if such an email was sent for this specific vulnerability.
This incident is part of a concerning pattern for SmarterMail. Less than a month prior, the Cyber Security Agency of Singapore (CSA) disclosed details of a maximum-severity flaw (CVE-2025-52691, CVSS 10.0) in the same software that also led to remote code execution. The recurring critical vulnerabilities in a widely-used enterprise email platform underscore the importance of rapid patching and transparent communication from vendors.
Practical Takeaways for Administrators
- Patch Immediately: If you are running SmarterMail, ensure you are on Build 9511 or later. The speed of exploitation after the patch release demonstrates that attackers are actively monitoring for and reverse-engineering fixes.
- Monitor Logs: Scrutinize your server logs for any access to the
/api/v1/auth/force-reset-passwordendpoint, especially between January 15 and 17, 2026. Look for requests with theIsSysAdminparameter set totrue. - Audit Admin Accounts: Verify all system administrator accounts. If you discover unexpected accounts or suspect a breach, immediately reset all admin passwords and review system integrity.
- Demand Transparency: Encourage your software vendors to provide detailed security advisories. Vague release notes hinder your ability to perform effective risk assessment and incident response.
- Implement Layered Security: While patching is critical, consider additional security controls. For example, restrict access to administrative APIs to trusted IP ranges, and monitor for unusual command execution patterns on the server host.
The SmarterMail exploit serves as a stark reminder that the window between patch release and active exploitation is shrinking. Organizations must prioritize patch management and maintain a healthy skepticism of vendor communications, especially when security details are omitted.
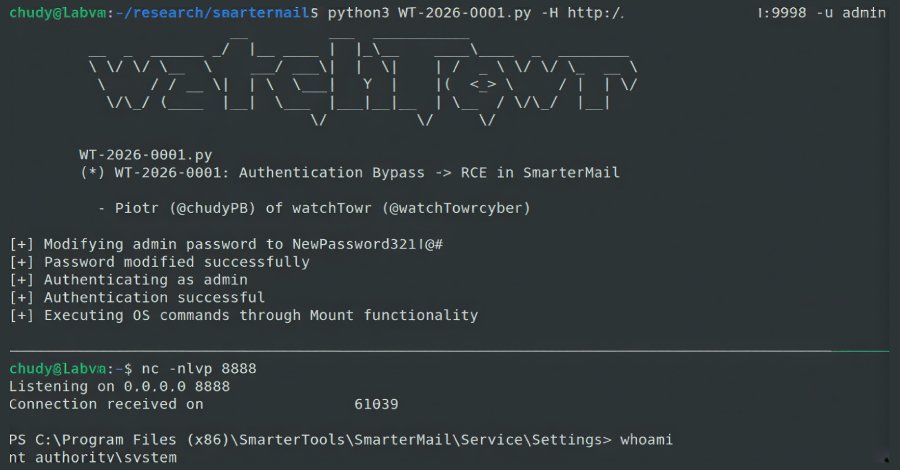
Featured image: A visual representation of the SmarterMail vulnerability chain, from authentication bypass to remote code execution.
Related Links:
- watchTowr Labs Research Blog (For detailed technical analysis)
- SmarterTools Official Site (For product information and updates)
- SmarterTools Community Portal (Where the initial exploitation was reported)
- Cyber Security Agency of Singapore (CSA) Advisory on CVE-2025-52691 (For context on previous SmarterMail vulnerabilities)

Comments
Please log in or register to join the discussion