Threat actors weaponized critical SmarterMail vulnerabilities within days of disclosure, sharing exploits via Telegram channels and enabling ransomware attacks, highlighting email servers as high-risk identity infrastructure.

Underground Telegram channels have become ground zero for the rapid weaponization of critical vulnerabilities in SmarterMail email servers, with threat actors sharing proof-of-concept exploits and stolen credentials within hours of public disclosure. This accelerated attack pipeline demonstrates how quickly ransomware groups capitalize on new security flaws in exposed infrastructure.
Security researchers monitoring these channels observed defenses being breached by attackers exploiting CVE-2026-24423 and CVE-2026-23760 – two critical flaws scoring 9.3 on the CVSS scale. CVE-2026-24423 enables unauthenticated remote code execution (RCE), allowing attackers to run arbitrary commands without user interaction. Its companion vulnerability, CVE-2026-23760, bypasses authentication controls and enables password resets for privileged accounts.
"These vulnerabilities create a perfect storm," explains a Flare security analyst. "Attackers combine RCE with credential theft to achieve full server control. Since SmarterMail often holds elevated trust positions in networks yet receives less monitoring than endpoints, it's an ideal initial access point for lateral movement."
Real-World Impact
This exploit chain isn't theoretical. SmarterTools disclosed they were breached in January 2026 when attackers exploited an unpatched internal SmarterMail server. The intruders moved laterally through Active Directory-connected networks before being contained by segmentation. In separate incidents, ransomware operators used the same vulnerabilities for initial access, staging attacks before deploying encryption payloads – a pattern observed in Warlock ransomware operations.
Why Email Servers Are Prime Targets
Email infrastructure sits at a critical security intersection:
- Hosts domain authentication tokens and password reset functions
- Contains organizational communication graphs
- Integrates with directory services
- Often has network-level trust relationships
Compromising email servers effectively compromises organizational identity systems. Recent Shodan scans identified 1,185 internet-exposed SmarterMail servers vulnerable to these flaws, predominantly in the United States.
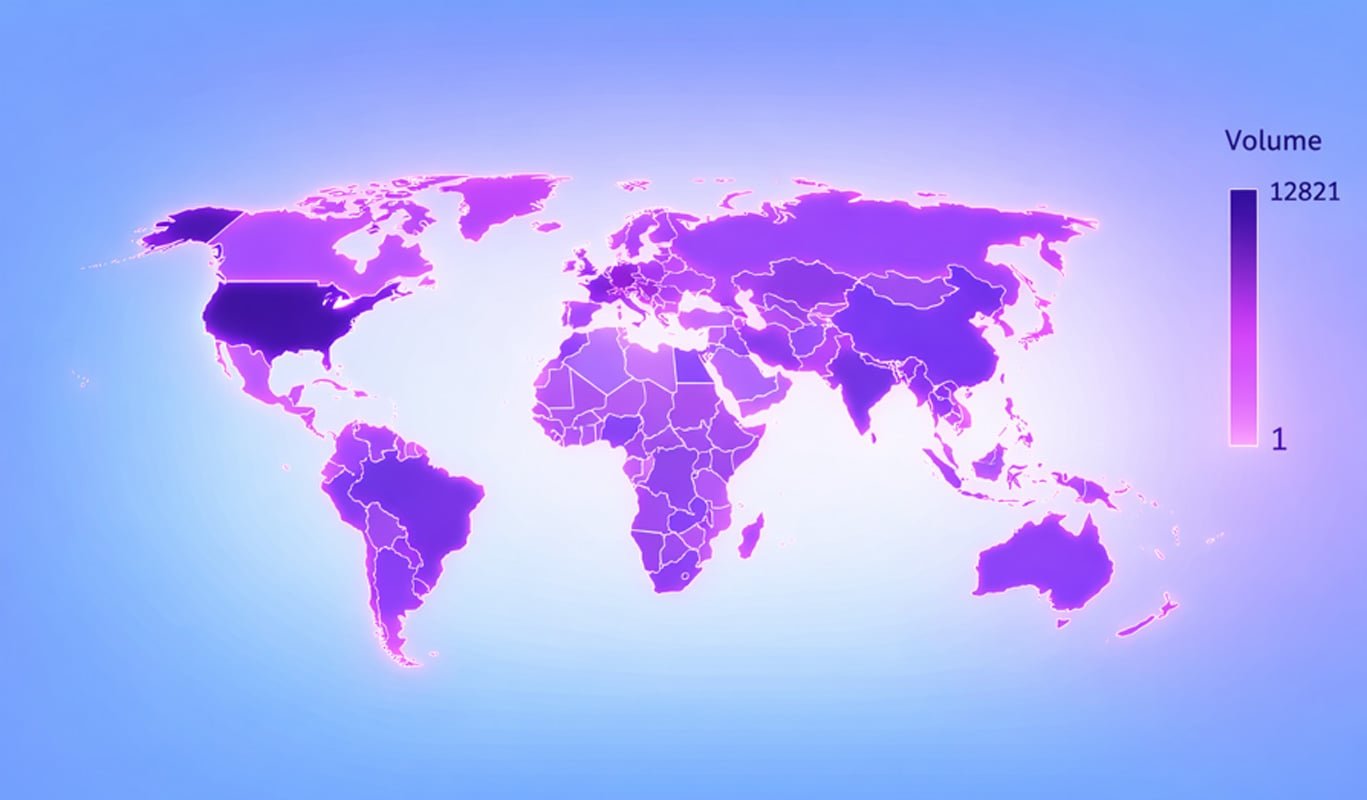 Geographical distribution of vulnerable SmarterMail servers (Source: Flare)
Geographical distribution of vulnerable SmarterMail servers (Source: Flare)
Underground Weaponization Timeline
Telegram channels accelerated exploitation:
- Day 0: Vulnerabilities publicly disclosed
- Within 24 hours: First mentions in Arabic and Spanish cybercrime channels
- 48-72 hours: Proof-of-concept exploits circulating
- 1 week: Admin credential dumps and offensive tools available
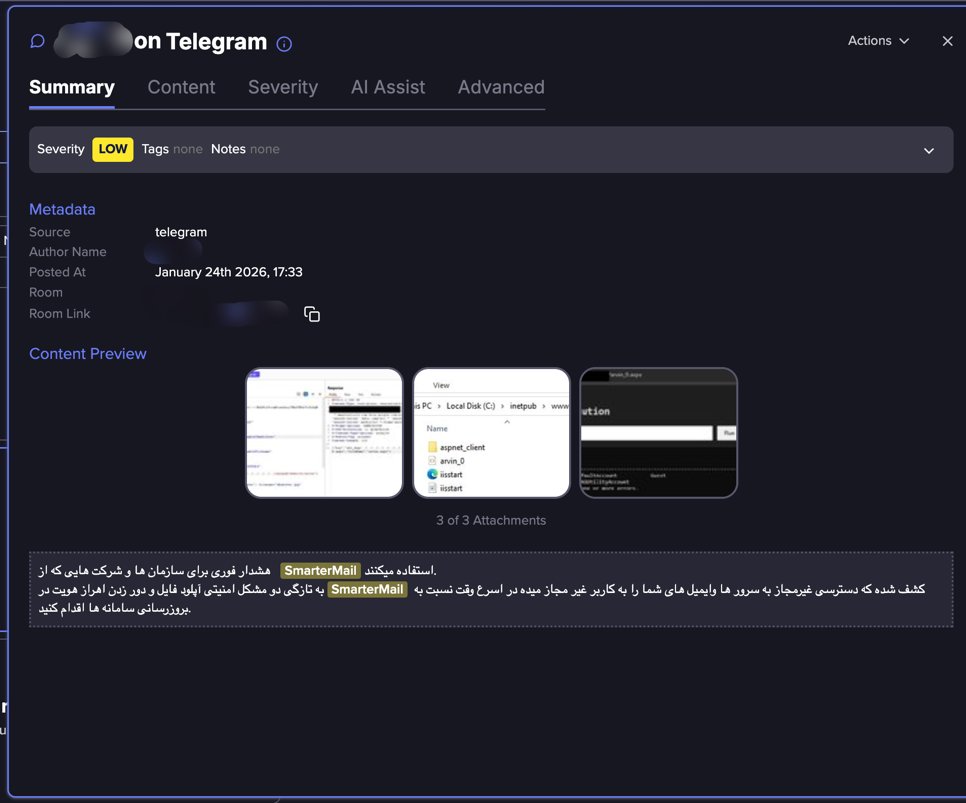 Telegram channel demonstrating SmarterMail exploit (Source: Flare)
Telegram channel demonstrating SmarterMail exploit (Source: Flare)
The Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2026-24423 to its Known Exploited Vulnerabilities Catalog in February 2026 after confirming ransomware exploitation.
Defense Recommendations
Treat email servers as critical identity infrastructure:
- Patch Urgency: Apply SmarterMail updates immediately (Build 9511+)
- Network Segmentation: Isolate email servers from internal networks
- Enhanced Monitoring: Detect unusual activities like:
- Bulk admin password resets
- Unusual outbound connections from mail servers
- Scheduled task creation
- Credential Rotation: Reset all administrator credentials post-patching
- Threat Hunting: Search for artifacts like DFIR tools or unexpected processes
"The timeline from vulnerability disclosure to ransomware deployment has shrunk to days," warns the Flare team. "Organizations that treat email servers as mere messaging platforms rather than identity brokers will remain vulnerable to these intrusion pipelines."
For continuous monitoring of emerging threats in underground channels, security teams can explore threat intelligence platforms. SmarterMail administrators should reference the official security bulletin for patching guidance.

Comments
Please log in or register to join the discussion