Security researchers demonstrated 37 zero-day vulnerabilities on the first day of Pwn2Own Automotive 2026, including a root compromise of Tesla's Infotainment System and multiple electric vehicle charging stations, highlighting critical security gaps in modern automotive technology.
The automotive industry's most anticipated security showdown delivered a sobering reality check this week. At Pwn2Own Automotive 2026 in Tokyo, security researchers exploited 37 zero-day vulnerabilities in the first 24 hours alone, demonstrating how modern vehicles and their supporting infrastructure remain vulnerable to sophisticated attacks. The most notable achievement came from Synacktiv Team, who successfully hacked a Tesla Infotainment System and earned $516,500 in cash awards.

The Tesla Compromise: A Chained Attack
Synacktiv Team's attack on the Tesla Infotainment System followed a classic but effective pattern. They began with an information leak vulnerability that exposed sensitive system data, then chained it with an out-of-bounds write flaw to achieve root permissions. This USB-based attack demonstrates how seemingly minor vulnerabilities can be combined to create catastrophic security breaches.
"The Tesla Infotainment System represents a complex attack surface," explains a security researcher familiar with automotive systems. "It combines infotainment functions with vehicle controls, creating a bridge between consumer applications and critical automotive systems. A root compromise here isn't just about media playback—it's about potential access to vehicle networks."
The attack highlights a fundamental challenge in modern vehicle architecture: the convergence of infotainment and vehicle control systems. While manufacturers implement security boundaries, the shared hardware and software stacks create potential pathways for attackers to pivot from entertainment systems to critical vehicle functions.
Beyond Tesla: A Widespread Vulnerability Landscape
The Tesla hack was just one of many successful exploits demonstrated at Pwn2Own Automotive 2026. The competition revealed systemic vulnerabilities across the automotive ecosystem:
Electric Vehicle Charging Infrastructure
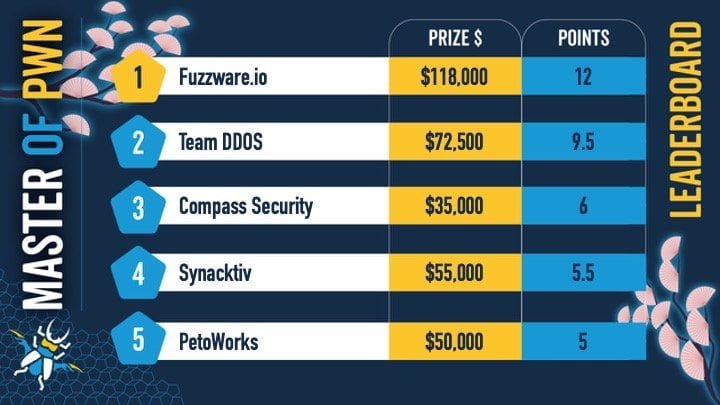
- Alpitronic HYC50 Charging Station: Hacked by Fuzzware.io for $118,000 total
- Autel MaxiCharger: Multiple teams targeted this charger, with successful exploits earning $50,000 each
- ChargePoint Home Flex: Compromised by Team DDOS
- Grizzl-E Smart 40A: Successfully hacked by Team DDOS
- Phoenix Contact CHARX SEC-3150: PetoWorks chained three zero-days to gain root privileges
In-Vehicle Infotainment Systems
- Sony XAV-9500ES: Synacktiv Team gained root-level code execution by chaining three vulnerabilities
- Kenwood DNR1007XR: Hacked by Fuzzware.io
The Economics of Automotive Security
Pwn2Own Automotive 2026 has already awarded $886,250 in cash prizes, with more to come as the competition continues through January 23. The substantial rewards reflect the critical nature of these vulnerabilities and the automotive industry's recognition of the security gap.
The competition follows a responsible disclosure model. Vendors have 90 days to develop and release security fixes before TrendMicro's Zero Day Initiative publicly discloses the vulnerabilities. This timeline balances the need for immediate vendor action with the reality that automotive patches often require extensive testing due to safety-critical implications.
Historical Context: A Growing Problem
The 2026 event continues a concerning trend. In 2025, researchers collected $886,250 after exploiting 49 zero-day vulnerabilities. The inaugural Pwn2Own Automotive in 2024 was even more dramatic, with $1,323,750 awarded for 49 zero-day bugs, including multiple Tesla compromises.
This pattern suggests that automotive security vulnerabilities aren't decreasing despite increased attention. The complexity of modern vehicles—with their dozens of electronic control units (ECUs), complex software stacks, and connectivity features—creates an expanding attack surface that outpaces security hardening efforts.
The Technical Reality: Why These Systems Are Vulnerable
Modern automotive systems face unique security challenges:
Complexity and Integration: Vehicles now contain 100+ million lines of code across multiple ECUs. The infotainment system often shares hardware and software components with other vehicle systems, creating potential cross-contamination risks.
Legacy and Modern Code: Many automotive systems run on modified versions of older operating systems or real-time operating systems that weren't designed with modern security threats in mind.
Supply Chain Issues: Automotive manufacturers rely on hundreds of suppliers for software components. A vulnerability in a single supplier's code can affect multiple vehicle models and manufacturers.
Update Challenges: Unlike consumer electronics, automotive updates must undergo rigorous safety testing. This means security patches can take months to reach vehicles, leaving them vulnerable in the interim.
Practical Implications for Vehicle Owners and Manufacturers
For vehicle owners, these findings underscore the importance of:
Keeping Software Updated: While automotive updates are slower than consumer electronics, they're critical for security. Enable automatic updates where available.
Understanding Connected Features: Every connected feature—Wi-Fi, Bluetooth, cellular, USB—creates potential attack vectors. Consider disabling unnecessary connectivity when not in use.
Physical Security: Many automotive attacks require physical access. Be mindful of where you park and who has access to your vehicle's ports.
For manufacturers, the path forward requires:
Security by Design: Implementing security from the earliest design phases, not as an afterthought.
Regular Security Audits: Conducting continuous security testing, including penetration testing and bug bounty programs.
Isolation Architecture: Implementing proper security boundaries between infotainment and critical vehicle systems.
Rapid Response Capability: Developing processes to quickly identify, patch, and deploy security updates.
The Broader Automotive Security Landscape
Pwn2Own Automotive represents just one facet of automotive security research. The competition provides valuable data for the industry, revealing real-world vulnerabilities that might otherwise remain hidden until exploited by malicious actors.
The automotive industry's response to these challenges will be critical. As vehicles become more connected, autonomous, and software-defined, the security implications extend beyond individual vehicles to entire transportation ecosystems. A compromised charging network could affect thousands of vehicles simultaneously. A vulnerability in a popular infotainment system could impact millions of cars.
Looking Ahead
The competition continues through January 23, with more targets scheduled for attack. The remaining challenges will test researchers' abilities to compromise additional charging stations, navigation systems, and vehicle operating systems.
Each successful exploit provides valuable data for manufacturers, security researchers, and regulators. The 90-day disclosure timeline creates urgency for vendors while allowing time for proper patch development. However, the automotive industry must recognize that patching vulnerabilities is only part of the solution—preventing them in the first place requires fundamental changes in how vehicles are designed, built, and maintained.
The 37 zero-days demonstrated in just one day at Pwn2Own Automotive 2026 serve as a stark reminder: as vehicles become more connected and software-defined, security can no longer be an afterthought. The automotive industry must invest in security with the same rigor it applies to safety engineering, recognizing that in the modern automotive landscape, security is safety.
Related Resources:

Comments
Please log in or register to join the discussion