The curl project is terminating its long-running bug-bounty program, citing an overwhelming flood of low-quality, AI-generated reports that have drowned out legitimate security research and taken a severe mental toll on maintainers. The decision marks a pivotal moment for open-source security, where the incentive structure designed to attract researchers has instead attracted a deluge of noise.
The curl project, a foundational tool embedded in billions of devices worldwide, has made a difficult but decisive choice. After more than five years of running a bug-bounty program that has paid out over $100,000 and confirmed 87 vulnerabilities, the project will officially terminate all monetary rewards for security reports on January 31, 2026. This isn't a story of failure, but rather a sobering reflection on how the security research ecosystem has been warped by the very incentives meant to improve it.
Daniel Stenberg, curl's creator and maintainer, announced the change in a detailed blog post that reads less like a corporate announcement and more like a weary confession from the front lines of open-source maintenance. The program, launched in 2019 with Hackerone as a partner and funded by the Internet Bug Bounty project, initially succeeded in its mission. It attracted skilled researchers, uncovered genuine vulnerabilities, and demonstrably improved curl's security posture. For years, the program maintained a healthy 15% confirmation rate—meaning roughly one in seven reports led to a confirmed vulnerability worth paying for.
But the landscape shifted dramatically in 2024 and 2025. The confirmation rate plummeted to below 5%, meaning fewer than one in twenty submissions represented real security issues. The culprit, according to Stenberg, is twofold: an explosion of AI-generated "slop" reports combined with a decline in the quality of human-submitted reports, which were increasingly influenced by AI tools. The result is a firehose of noise that requires significant mental energy to debunk, creating what Stenberg describes as a "serious mental toll" that "hamper[s] our will to live."
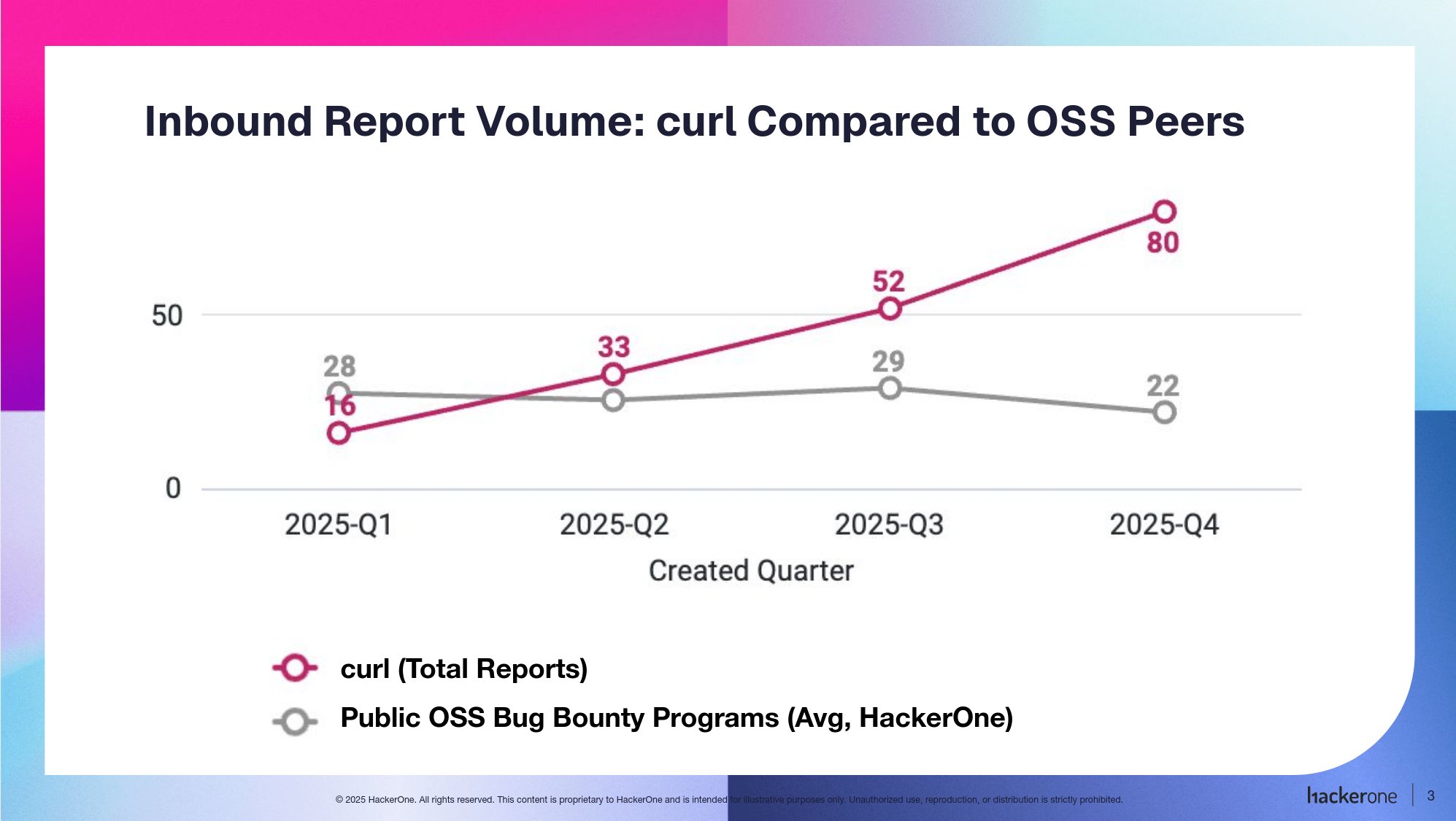
The data supports this anecdotal experience. When compared to other open-source bug-bounty programs on Hackerone—such as Ruby, Node, and Rails—curl's inbound report volume has skyrocketed while others remained flat or declined. The pink line representing curl's report volume in the provided chart shows a sharp upward trajectory, diverging significantly from the broader cohort. This discrepancy suggests that the monetary incentive, while attracting legitimate researchers, also makes the project an attractive target for low-effort, high-volume submissions. The reputation system and program settings on Hackerone proved insufficient to filter this noise.
Beyond the sheer volume, Stenberg identifies a troubling shift in attitude among some reporters. He describes a "bad faith" approach where submitters attempt to "twist whatever they find into something horribly bad and a critical vulnerability" rather than genuinely contributing to curl's improvement. These reporters, he notes, will argue extensively for their specific finding but rarely help write fixes or engage in long-term collaboration. This adversarial dynamic contrasts sharply with the collaborative spirit that open-source security ideally fosters.
The decision to end the bug-bounty program represents a fundamental rethinking of how curl will handle security reports going forward. The project will no longer offer monetary rewards for any severity level, effectively removing the financial incentive that has driven much of the recent noise. Simultaneously, curl is moving away from Hackerone as its primary reporting channel, directing researchers instead to GitHub's private vulnerability reporting feature or directly to the security team via email. This change serves both practical and symbolic purposes: it makes the shift immediately visible and aligns the reporting process with the project's core infrastructure.
Critically, curl's maintainers believe they can maintain—and potentially even improve—security without the bounty program. The hope is that by removing the monetary incentive, they will reduce the volume of low-quality submissions and free up time and mental energy for actual security work. Stenberg expresses confidence that the best researchers, those genuinely motivated by improving curl rather than earning rewards, will continue to report vulnerabilities through the new channels.
The project has also taken a hard line on AI-generated submissions, committing to immediately ban and publicly ridicule those who submit such reports. This aggressive stance reflects the frustration with the current state of affairs and serves as a deterrent against future abuse. For pull requests, curl has not experienced the same AI-induced problems, likely because automated testing and CI pipelines (with 200 jobs running) provide effective quality gates that don't require human intervention until contributions meet a minimum standard.
The broader implications of this decision extend beyond curl itself. It highlights a growing tension in the open-source security world: the balance between incentivizing legitimate research and protecting maintainers from abuse. Bug-bounty programs were created to address the chronic underfunding of open-source security, providing financial rewards that make security research more viable. But as AI tools lower the barrier to generating seemingly technical reports, these programs risk becoming victims of their own success, attracting both genuine researchers and opportunistic spammers.

Other projects have reported similar issues, though curl appears to have been hit particularly hard. The exact reasons remain speculative—perhaps curl's ubiquity makes it a more attractive target, or its specific reporting process may be more vulnerable to exploitation. What's clear is that the current model is unsustainable for at least this project, and the decision to abandon bounties may force a broader conversation about how open-source security can be funded and managed in an era of AI-assisted reporting.
Stenberg explicitly rejects one alternative solution that has been suggested: charging researchers a fee to submit reports. He argues this would create international complexity, add maintenance burden, and potentially exclude legitimate researchers who cannot afford the fee. While acknowledging that this approach might become necessary later, curl is choosing the simpler path of elimination for now.
The project's transparency about this decision is noteworthy. Rather than quietly discontinuing the program, curl's team has been forthright about the challenges they face, sharing data and personal experiences that illuminate the difficulties of modern open-source maintenance. This transparency extends to future plans: curl will continue to evaluate the situation and may make further changes if the volume of reports doesn't decrease as expected.
For the security research community, this represents a significant shift. The termination of curl's bug-bounty program removes a notable opportunity for researchers to earn rewards while contributing to a critical piece of internet infrastructure. It also serves as a cautionary tale about the potential unintended consequences of financial incentives in open-source security. As AI tools become more sophisticated and accessible, the line between legitimate research and automated spam will continue to blur, forcing projects to develop new strategies for maintaining security without burning out their maintainers.
The curl team's decision to prioritize mental health and maintainability over the potential benefits of a bounty program reflects a growing recognition that open-source sustainability depends on more than just code quality—it requires protecting the humans behind the projects. As Stenberg notes, the goal is to "prevent more people pouring sand into the machine" and to reduce wasted time and effort, allowing the team to focus on genuine security improvements rather than debunking false reports.
This change will likely have ripple effects across the open-source ecosystem. Other projects watching curl's experience may reconsider their own bounty programs or implement stricter filters and requirements. The conversation about how to fund open-source security continues to evolve, with this decision adding a new dimension: not just how to pay for security, but how to do so without creating perverse incentives that undermine the very goals the program seeks to achieve.
Ultimately, curl's story is one of adaptation. The project that has been a cornerstone of internet infrastructure for decades is once again evolving to meet new challenges. By ending its bug-bounty program, curl isn't giving up on security—it's redefining what effective security looks like in an age where AI can generate convincing but empty reports at scale. The success of this experiment will be measured not just in vulnerability counts, but in the health and sustainability of the team that keeps curl running. For now, the project is betting that removing financial incentives will lead to better security outcomes, a conclusion that will be tested in the months and years to come.

Comments
Please log in or register to join the discussion