Criminal IP's integration with IBM QRadar brings AI-powered threat intelligence directly into security workflows, enabling faster incident response and more accurate threat prioritization.
Security teams face an overwhelming volume of alerts daily, with many lacking the critical context needed to distinguish genuine threats from noise. The integration of Criminal IP with IBM QRadar SIEM and SOAR addresses this challenge by embedding real-time, AI-powered threat intelligence directly into existing security workflows, enabling faster, more informed decision-making without adding operational complexity.

Real-Time Threat Intelligence at the Network Edge
The integration begins at the network perimeter, where firewall traffic logs flow into IBM QRadar SIEM. Criminal IP's API analyzes each observed IP address in real-time, automatically classifying them into High, Medium, or Low risk levels based on threat intelligence derived from internet exposure. This immediate risk assessment transforms raw network data into actionable intelligence.
Security Operations Center (SOC) teams can now monitor both inbound and outbound traffic with enhanced visibility, identifying high-risk IPs that might otherwise blend into the noise of normal network activity. When suspicious communication is detected, analysts can immediately prioritize response actions such as access blocking or escalation, all within the familiar QRadar interface they already use daily.
Interactive Investigation Without Tool Switching
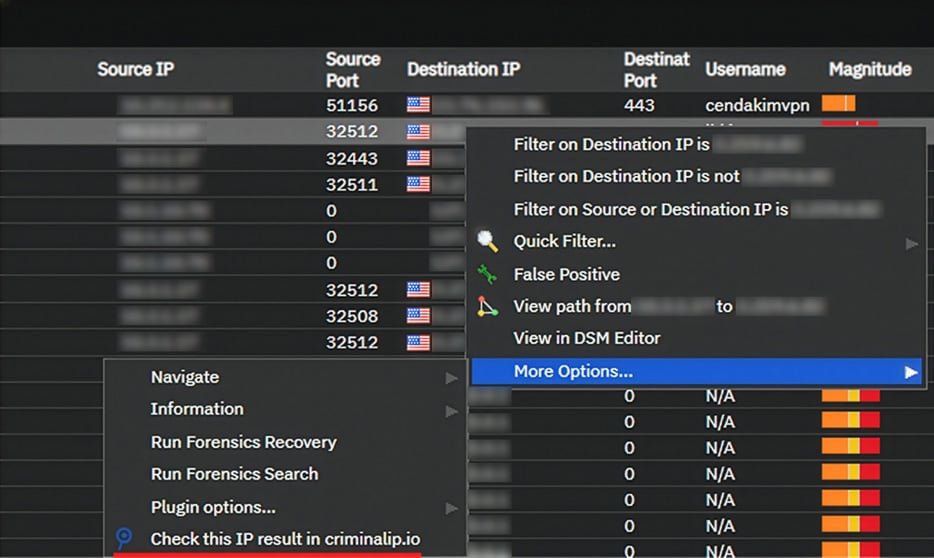
One of the most significant workflow improvements comes from Criminal IP's integrated lookup capability within QRadar Log Activity. Analysts can right-click on any IP address displayed in traffic logs and instantly access a detailed Criminal IP report. These reports provide comprehensive context including:
- Historical behavior patterns of the IP address
- Threat indicators and reputation data
- External exposure signals and associated risks
- Connections to known malicious infrastructure
This in-context investigation eliminates the need to copy IP addresses, switch to external tools, and manually cross-reference threat intelligence databases. During time-sensitive investigations, this streamlined workflow can mean the difference between containing a threat quickly and allowing it to spread.
Automated Enrichment in SOAR Workflows
The integration extends beyond SIEM into IBM QRadar SOAR, where pre-built playbooks automatically enrich incident artifacts with Criminal IP intelligence. Two specialized playbooks handle different types of threats:
Criminal IP: IP Threat Service - Enriches IP address artifacts with comprehensive threat context, including risk scoring and reputation data.
Criminal IP: URL Threat Service - Performs both lite and full URL scans, returning results as artifact hits or incident notes within SOAR cases.
These automated enrichment capabilities significantly reduce the manual workload on analysts. Instead of performing repetitive lookups across multiple threat intelligence sources, analysts receive consolidated, actionable intelligence directly within their incident response workflows. This automation not only speeds up response times but also improves consistency in how threat intelligence is applied across different incidents.
Intelligence-Driven Detection and Response
The true value of this integration lies in its ability to combine QRadar's powerful correlation, investigation, and response capabilities with Criminal IP's context-rich external threat intelligence. This combination addresses one of the most persistent challenges in modern SOC operations: improving detection accuracy while managing increasing alert volumes.
By incorporating real-world internet exposure data into the incident lifecycle, organizations can reduce false positives and focus resources on genuine threats. The integration supports more confident decision-making throughout the detection and response process, from initial alert triage through final remediation.
AI-Powered Threat Intelligence Foundation
Criminal IP's effectiveness stems from its AI and OSINT-powered platform, which continuously analyzes internet-wide exposure to identify malicious indicators. The platform detects a wide array of threats including:
- Command and Control (C2) servers
- Indicators of Compromise (IOCs)
- Masking services such as VPNs, proxies, and anonymous networks
- Malicious domains and URLs
This comprehensive coverage ensures that security teams have visibility across the full spectrum of potential threats, from sophisticated nation-state actors to common cybercrime operations.
Practical Benefits for Security Teams
The integration delivers several concrete benefits that address real-world SOC challenges:
Faster Incident Response - By embedding threat intelligence directly into QRadar workflows, analysts can make decisions more quickly without switching between tools or waiting for manual lookups.
Improved Prioritization - Risk-based classification of IP addresses helps teams focus on the most critical threats first, optimizing limited security resources. Reduced Manual Effort - Automated enrichment in SOAR workflows eliminates repetitive tasks, allowing analysts to focus on complex investigations and strategic security initiatives. Enhanced Detection Accuracy - External threat context helps distinguish genuine threats from benign activity, reducing false positives and alert fatigue.
Industry Context and Adoption
IBM QRadar's widespread adoption by enterprises and public-sector organizations makes this integration particularly significant. As a central platform for security monitoring, automation, and incident response, QRadar serves as the operational hub for many SOCs. By embedding Criminal IP intelligence directly into this environment, organizations can leverage external threat context without disrupting established workflows or requiring additional training.
The integration reflects a broader industry trend toward intelligence-driven security operations, where external threat context is seamlessly incorporated into detection and response processes. As attack surfaces continue to expand and threat actors become more sophisticated, this approach becomes increasingly critical for maintaining effective security postures.
Implementation and Integration
The API-first architecture of Criminal IP ensures seamless integration with existing security workflows. Organizations can implement the integration without significant infrastructure changes or operational overhead. The pre-built playbooks for QRadar SOAR provide immediate value, while the flexible API allows for customization to meet specific organizational needs.
For security teams looking to enhance their QRadar deployment with external threat intelligence, the Criminal IP integration offers a practical, immediately deployable solution that delivers measurable improvements in detection accuracy and response efficiency.
As Byungtak Kang, CEO of AI SPERA, noted, this integration underscores the growing importance of real-time, exposure-based intelligence in modern SOC environments. By bringing external threat context directly into SIEM and SOAR workflows, Criminal IP helps organizations make faster, more informed decisions while maintaining operational simplicity.

Comments
Please log in or register to join the discussion