A critical vulnerability in OnePlus's Android implementation allows malicious apps to access SMS content without permissions or user interaction. Despite seven disclosure attempts by Rapid7 over four months, OnePlus failed to respond, leaving millions of devices exposed. The unpatched flaw enables attackers to reconstruct private messages via SQL injection attacks.
Silent SMS Extraction: Unpacking OxygenOS's Critical Permission Bypass

Security researchers at Rapid7 have uncovered a severe vulnerability (CVE-2025-10184) in OnePlus's OxygenOS that grants any installed application unrestricted access to SMS messages and metadata—no permissions required. This fundamental breakdown in Android's security model affects all OxygenOS versions from 12 through 15, putting devices like the OnePlus 8T and 10 Pro series at immediate risk.
Anatomy of the Permission Bypass
The flaw stems from OnePlus's modifications to Android's core Telephony package. Unlike stock Android, OxygenOS introduces additional exported content providers (PushMessageProvider, PushShopProvider, ServiceNumberProvider) without proper write permissions. Crucially, these components lack the READ_SMS permission declaration, creating a free-for-all access scenario.
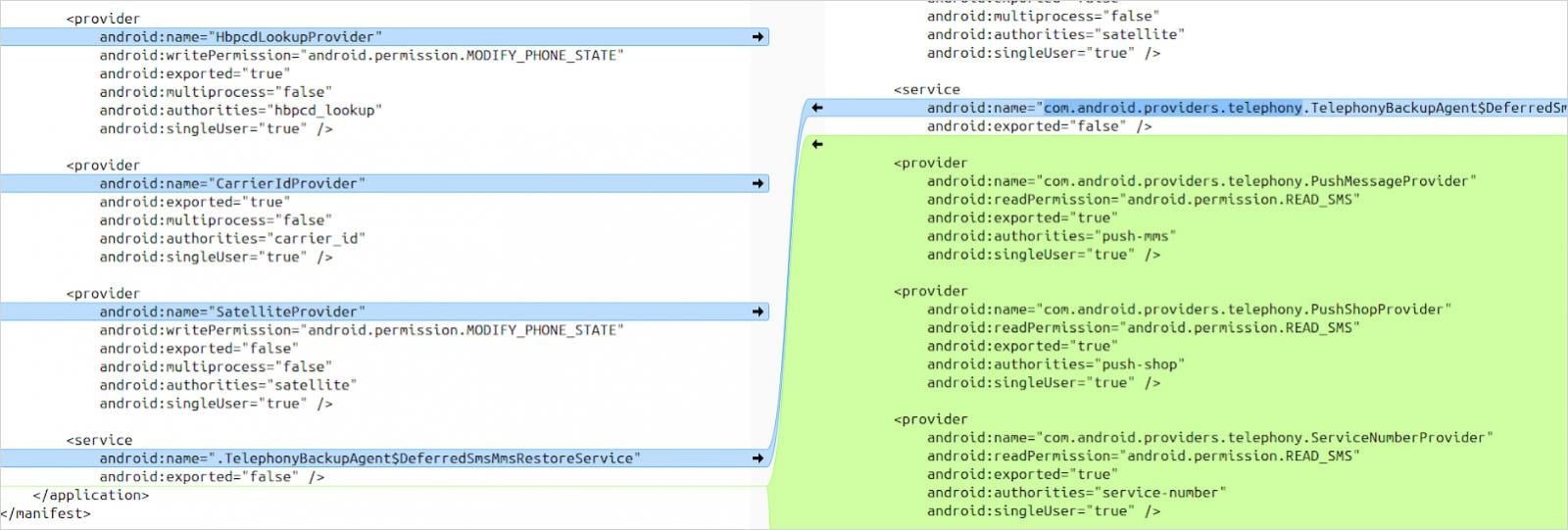 Extra providers added by OnePlus to the Telephony package (Source: Rapid7)
Extra providers added by OnePlus to the Telephony package (Source: Rapid7)
Worse yet, these providers accept unsanitized inputs, enabling blind SQL injection attacks. As Rapid7's report explains:
"By using an algorithm to repeat this process for each character in each row... it’s possible to exfiltrate the database content, using the return value from the update method as an indicator of true/false."
This technique allows attackers to reconstruct SMS content character-by-character from the device's database when two conditions are met:
- The target table contains at least one row
- The provider permits
insert()operations (enabling creation of dummy rows) - The SMS table resides in the same SQLite database
 PoC demonstrating SMS content inference via SQL injection (Source: Rapid7)
PoC demonstrating SMS content inference via SQL injection (Source: Rapid7)
Millions of Devices Exposed
The vulnerability spans virtually all recent OnePlus devices:
| Device Model | OxygenOS Version | Affected Build Numbers |
|---|---|---|
| OnePlus 8T (KB2003) | 12 | KB2003_11_C.3 |
| OnePlus 10 Pro 5G | 14-15 | NE2213_14.0.0.700(EX01) |
| NE2213_15.0.0.502(EX01) | ||
| NE2213_15.0.0.700(EX01) | ||
| NE2213_15.0.0.901(EX01) |
Rapid7 confirmed exploitability across multiple device generations, noting the flaw resides in core Android components—suggesting broader impact beyond tested models.
Disclosure Failures and Delayed Response
Rapid7 initiated contact with OnePlus on May 1, 2025, followed by six additional attempts through August 16—all met with silence. Only after public disclosure did OnePlus acknowledge the report. This four-month radio silence highlights critical breakdowns in vendor security coordination.
Mitigation Strategies for Affected Users
Until OnePlus releases patches, security professionals recommend:
- Minimize installed apps: Restrict installations to essential, vetted applications
- Abandon SMS 2FA: Switch to authenticator apps like Google Authenticator
- Use encrypted messaging: Favor Signal/WhatsApp for sensitive communications
- Monitor for updates: Vigilantly check for OxygenOS security patches
This vulnerability underscores the risks of OEM Android modifications and the urgent need for transparent vendor response protocols. With SMS often serving as an authentication backbone, the flaw exposes both personal data and security infrastructure to silent compromise.
Source: BleepingComputer, Rapid7 Technical Report

Comments
Please log in or register to join the discussion