Security researcher Jeremiah Fowler discovered a massive, unprotected database containing 149 million stolen login credentials from infostealer malware, affecting users across Gmail, Facebook, government portals, and cryptocurrency exchanges.
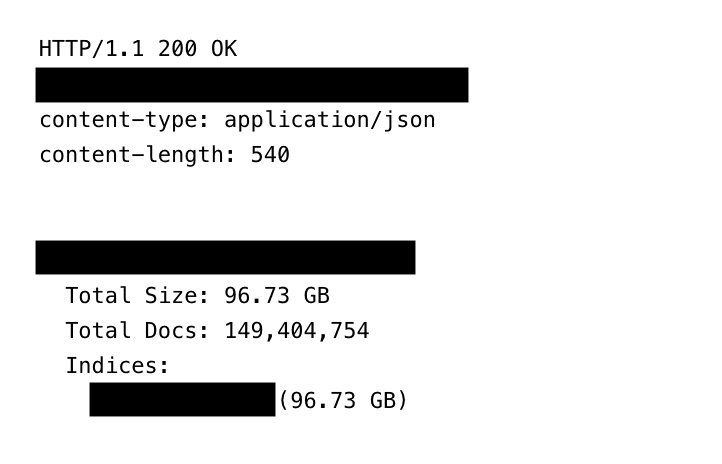
A security researcher recently discovered an unprotected database containing 149,404,754 unique login credentials. The collection required no password to access and was not encrypted, leaving nearly 100GB of sensitive data exposed to anyone who knew where to look.
Veteran security researcher Jeremiah Fowler found the database while conducting routine internet scans. The data wasn't just a simple list—it contained complete login packages: email addresses, usernames, passwords, and the specific URLs needed to access each account. Fowler reported his findings through ExpressVPN, noting the database was completely open. "The publicly exposed database was not password-protected or encrypted," he said.

The scope of compromised accounts spans nearly every online service. Consumer platforms dominate the list, with Gmail accounts at 48 million, Facebook at 17 million, and Instagram at 6.5 million. Streaming and email services were also heavily represented: Yahoo (4 million), Netflix (3.4 million), and Outlook (1.5 million). The breach even reached specialized platforms, including cryptocurrency exchanges like Binance (420,000 accounts) and content platforms like OnlyFans (100,000 accounts).

Perhaps most concerning, the database included credentials for .gov domains across multiple countries. Fowler warned that these government logins could enable targeted spear-phishing campaigns, impersonation attacks, or provide entry points into government networks.
How Infostealer Malware Harvests Data
The credentials likely came from infostealer malware—malicious software that operates silently on compromised devices. Once installed, these programs capture every keystroke, including login forms and passwords, then transmit the data back to attacker-controlled servers. The database Fowler discovered was specifically structured to automatically index and organize this stolen data for easy searching.
During the nearly month-long process of getting the database secured, Fowler watched the number of records actually increase. New victim data continued flowing in even as he worked to alert the hosting provider.
The Takedown Process
Locating the database owner proved impossible since the system contained no identifying information. Fowler had to work directly with the hosting provider, navigating through a global host and independent subsidiary before the data was finally secured. The slow, confusing process highlights a persistent problem in cybersecurity: identifying and shutting down malicious infrastructure often takes weeks, during which time attackers continue collecting data.
The Credential Stuffing Cascade
While the specific server is now offline, the 149 million credentials are almost certainly already distributed among criminal networks. These credentials fuel credential stuffing attacks, where criminals test stolen passwords across multiple services. Since many people reuse passwords, a single breach can unlock dozens of accounts. The data also enables identity theft, financial fraud, and highly convincing phishing emails that reference real account details.
Protection Strategies
This incident demonstrates that credential theft has become an industrialized operation. Fowler described it as highlighting "the global threat posed by credential-stealing malware." Users should take several defensive steps:
Assume exposure: With 149 million records, the probability that any given user is affected is high.
Password rotation: Start with email and financial accounts, then work through other services. This is only effective if combined with other measures.
Unique passwords: Never reuse credentials across sites. A password manager makes this practical.
Two-factor authentication: Enable 2FA on every service that offers it. Even if criminals have your password, they cannot access accounts without the second factor.
Malware scanning: Use reputable antivirus software to check for infostealers. Simply changing passwords won't help if malware remains active—it will just capture the new credentials.
Phishing vigilance: Be extra cautious with emails that reference account details or online activity. Criminals use the exposed data to craft convincing messages.
This breach follows other recent security changes in the ecosystem. Google recently ended Gmailify and POP3 support, tightening access controls across its platform as credential theft continues to escalate.


Comments
Please log in or register to join the discussion