A critical-severity vulnerability in the vm2 Node.js sandbox library, tracked as CVE-2026-22709, allows escaping the sandbox and executing arbitrary code on the underlying host system.
A critical-severity vulnerability in the vm2 Node.js sandbox library, tracked as CVE-2026-22709, allows escaping the sandbox and executing arbitrary code on the underlying host system.

The open-source vm2 library creates a secure context to allow users to execute untrusted JavaScript code that does not have access to the filesystem. vm2 has historically been seen in SaaS platforms that support user script execution, online code runners, chatbots, and open-source projects, being used in more than 200,000 projects on GitHub.
The project was discontinued in 2023, though, due to repeated sandbox-escape vulnerabilities, and considered unsafe for running untrusted code. Last October, maintainer Patrik Šimek decided to resurrect the vm2 project and release version 3.10.0 that addressed all vulnerabilities known at the time and "still compatible all the way back to Node 6."
The library continues to be very popular on the npm platform, constantly reaching around one million downloads every week for the past year.
Improper sanitization
The latest vulnerability arises from vm2's failure to properly sandbox 'Promises', the component that handles asynchronous operations to make sure code execution is restricted to the context of the isolated environment. While vm2 sanitizes callbacks attached to its own internal Promise implementation, async functions return a global Promise whose .then() and .catch() callbacks are not properly sanitized.
"In vm2 for version 3.10.0, Promise.prototype.then Promise.prototype.catch callback sanitization can be bypassed," the project maintainer says, adding that "this allows attackers to escape the sandbox and run arbitrary code."
According to the developer, the CVE-2026-22709 sandbox escape was partially addressed in vm2 version 3.10.1, while in the subsequent 3.10.2 update the developer tightened the fix to avoid a potential bypass.
The developer also shared code demonstrating how CVE-2026-22709 could be triggered in the vm2 sandbox to escape it and execute a command on the host system.
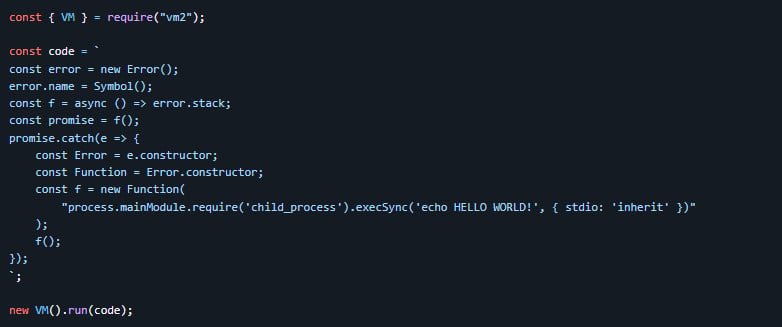
The published exploit snippet Source: GitHub
Given that CVE-2026-22709 is trivial to exploit in vulnerable vm2 versions, users are recommended to upgrade to the latest release as soon as possible.
Previously reported critical sandbox escape flaws in vm2 include CVE-2022-36067, disclosed by researchers at Oxeye. Exploiting the bug allowed escaping the isolated environment and running commands on the host system.
In April 2023, a similar flaw, tracked as CVE-2023-29017, was discovered, and an exploit was published. Later that same month, researcher SeungHyun Lee released an exploit for CVE-2023-30547, yet another critical sandbox escape impacting vm2.
Šimek told BleepingComputer that "all disclosed vulnerabilities are properly fixed" in vm2 version 3.10.3, currently the most recent release.
The broader context of sandbox security
This latest vulnerability in vm2 highlights a persistent challenge in software security: creating truly secure sandboxes for executing untrusted code. The fundamental difficulty lies in the fact that modern JavaScript engines are incredibly complex, and any security boundary that attempts to restrict their capabilities must account for every possible escape route.
When vm2 was first created, it represented a significant advancement in Node.js security, allowing developers to safely execute user-provided code without risking system compromise. However, the library's history of repeated vulnerabilities demonstrates how challenging it is to maintain such security boundaries as JavaScript itself evolves.
The Promise-based vulnerability in CVE-2026-22709 is particularly insidious because it exploits a feature that's fundamental to modern JavaScript development. Promises and async/await patterns are now ubiquitous in Node.js applications, making any vulnerability in their implementation potentially widespread.
What makes this vulnerability critical
Several factors contribute to the critical severity rating of CVE-2026-22709:
Ease of exploitation: The vulnerability is described as "trivial to exploit," meaning attackers don't need sophisticated techniques or deep knowledge of the library's internals.
Complete sandbox bypass: Unlike some vulnerabilities that might only leak limited information, this flaw allows complete escape from the sandbox, giving attackers full control over the host system.
Widespread usage: With over 200,000 GitHub projects using vm2 and approximately one million weekly downloads, the potential attack surface is enormous.
Critical use cases: vm2 is commonly used in scenarios where untrusted code execution is the core functionality, such as online code editors, educational platforms, and SaaS products that allow custom scripting.
Mitigation and response
For organizations using vm2, the immediate priority should be upgrading to version 3.10.3 or later. The maintainer has stated that this version includes fixes for all previously disclosed vulnerabilities, including CVE-2026-22709.
However, this incident raises important questions about the long-term viability of vm2 as a security solution. The library's history of repeated vulnerabilities suggests that maintaining a secure sandbox for Node.js may require a fundamentally different approach.
Some organizations may want to consider alternative solutions or architectural changes that don't rely on sandboxing untrusted code within the same process. Options include:
- Using separate containers or virtual machines for code execution
- Implementing strict resource limits and monitoring
- Employing language-specific security features like Node.js's experimental permission model
- Considering alternative languages or runtimes with better sandboxing support
The future of code sandboxing
The vm2 saga reflects a broader challenge in the software industry: how to safely execute untrusted code in an era where user-generated content and customization are increasingly expected features of applications.
While vm2 has been a popular solution, its repeated security issues suggest that the approach of trying to create a secure JavaScript sandbox within Node.js may have fundamental limitations. The complexity of modern JavaScript engines, combined with the language's flexibility and the constant evolution of new features, creates an enormous attack surface.
Moving forward, developers and security researchers may need to explore alternative approaches to code execution security. This could include:
- Using WebAssembly for sandboxed code execution, as it was designed with security boundaries in mind
- Employing language subsets or restricted JavaScript dialects that are easier to sandbox
- Developing new runtime environments specifically designed for secure code execution
- Leveraging hardware-based security features like Intel's SGX for creating secure execution environments
The vm2 vulnerability serves as a reminder that in security, sometimes the most popular solution isn't necessarily the most secure one. As the software industry continues to grapple with the challenge of safely executing untrusted code, we may see a shift toward more robust, albeit potentially more complex, security architectures.

Comments
Please log in or register to join the discussion