Freedom of the Press Foundation's open-source tool transforms potentially malicious PDFs, Office docs, and images into safe PDFs through containerized rasterization.
Digital documents remain a common attack vector for malware, with malicious PDFs and Office files frequently used in targeted attacks. Dangerzone, an open-source project by the Freedom of the Press Foundation, addresses this threat through an innovative rasterization approach that neutralizes embedded threats while preserving document content.
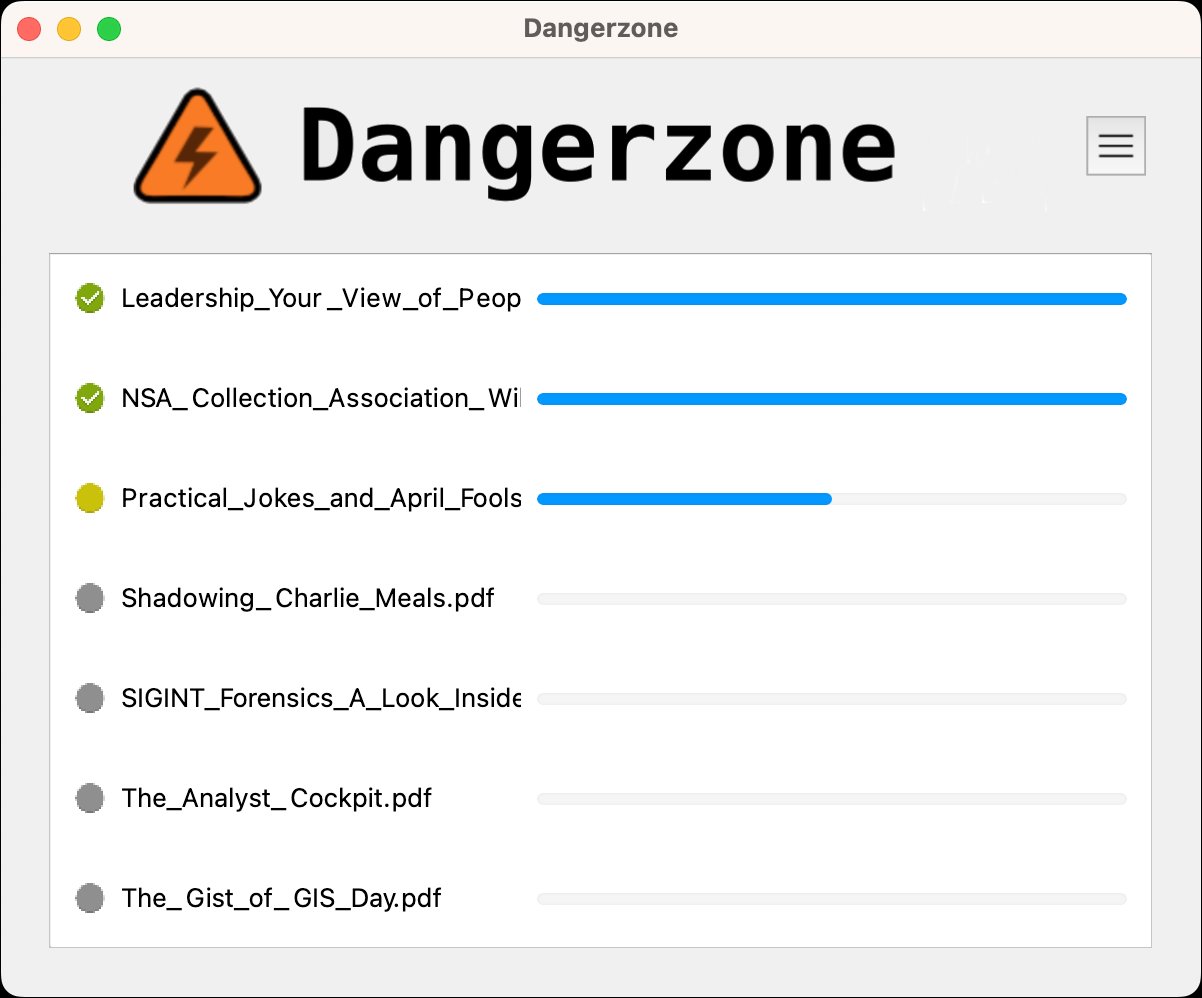
Here's how it works: Users submit potentially dangerous documents (PDFs, Word, Excel, images, etc.). Inside a containerized sandbox running gVisor—an application kernel written in Go that implements Linux system calls—Dangerzone first converts the document to PDF (if needed), then renders each page into raw pixel data (RGB values). This pixel data then exits the sandbox, where Dangerzone reconstructs it into a new, safe PDF document. The process intentionally discards all original document structure, scripts, and embedded objects that could contain malware.
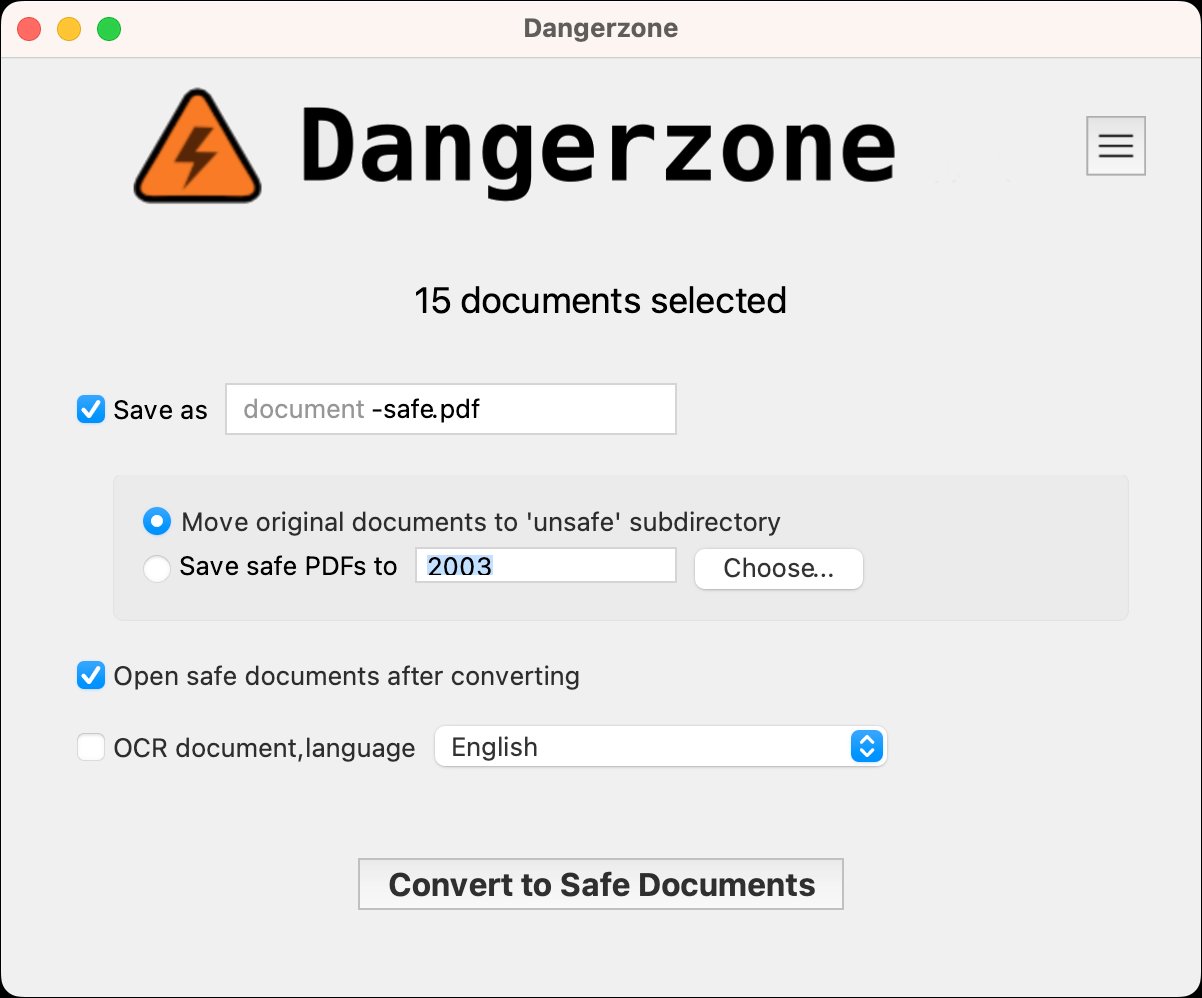
Key security features include:
- Airgap-compatible operation: Sandboxes have no network access
- gVisor isolation: Provides kernel-level security boundaries
- Optional OCR: Adds searchable text layers to output PDFs
- File compression: Reduces output file size
- Default handler integration: Prevents accidental opening of untrusted files
Supported formats include PDF, Microsoft Office (.docx, .xlsx, etc.), OpenDocument formats, EPUB, and common image types (JPG, PNG, SVG). Recent additions include Hancom HWP support.
In December 2023, Dangerzone underwent a security audit by Include Security. The audit revealed no high-risk vulnerabilities, with only 3 low-risk and 7 informational findings—a strong result for complex document processing software. Concurrently, the team launched a $3,000 Christmas Security Challenge inviting researchers to bypass its protections.
Platform support includes macOS, Windows, Ubuntu, Debian, Fedora, Qubes OS (beta), and Tails. The tool uses Docker/podman for containerization and operates without internet access by default, making it suitable for airgapped environments. As Freedom of the Press Foundation's Micah Lee explained, "This approach ensures that even if a document exploits a zero-day vulnerability in the rendering software, the attacker gains no persistent access."
Dangerzone is licensed under AGPLv3 and available on GitHub, with detailed documentation covering airgap updates and custom runtime configurations.
Comments
Please log in or register to join the discussion