Security researchers collected $1,047,000 in prize money after demonstrating 76 zero-day vulnerabilities affecting electric vehicle chargers, infotainment systems, and automotive operating systems during the three-day competition in Tokyo.
Security researchers walked away with $1,047,000 in prize money after exposing 76 zero-day vulnerabilities at Pwn2Own Automotive 2026, held January 21-23 in Tokyo during the Automotive World conference. The competition focused exclusively on automotive technologies, targeting the increasingly connected systems that power modern vehicles.

Targeting Critical Automotive Infrastructure
The competition structure revealed the breadth of attack surfaces in contemporary vehicles. Participants exploited vulnerabilities across three primary categories: fully patched in-vehicle infotainment (IVI) systems, electric vehicle chargers, and car operating systems like Automotive Grade Linux. These systems represent the convergence of consumer electronics and automotive engineering, introducing traditional software vulnerabilities into safety-critical environments.
Vendors receive a 90-day remediation window before Trend Micro's Zero Day Initiative publicly discloses exploited vulnerabilities. This coordinated disclosure process balances public safety concerns with the practical realities of developing patches for complex automotive systems that require extensive testing and regulatory approval.
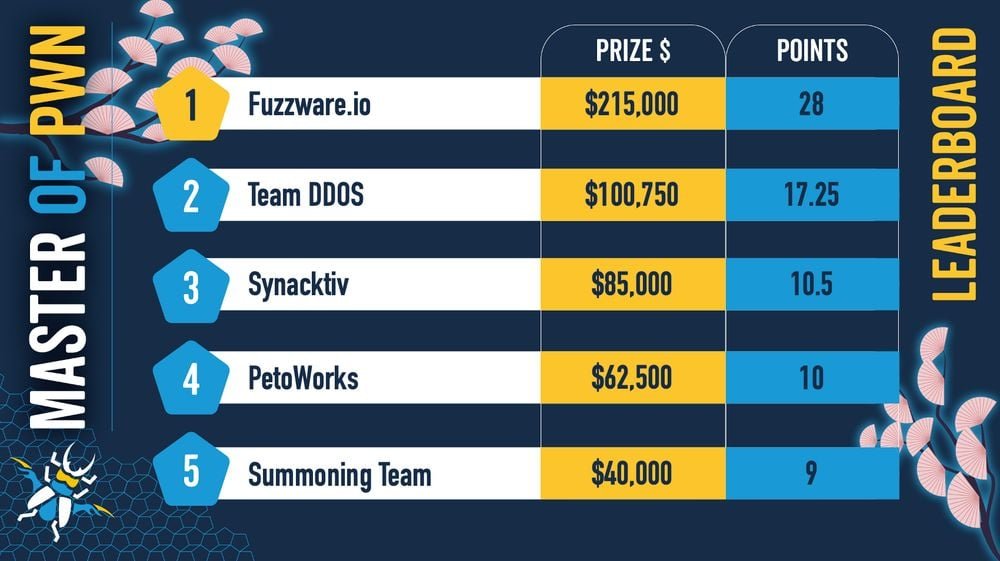
Team Fuzzware.io Dominates the Competition
Team Fuzzware.io secured first place with $215,000 in total earnings through systematic exploitation of charging infrastructure and infotainment systems. Their attack surface spanned multiple manufacturers and device categories:
Day One Successes:
- Alpitronic HYC50 Charging Station: $40,000
- Autel charger: $40,000
- Kenwood DNR1007XR navigation receiver: $38,000
Day Two Exploits:
- Phoenix Contact CHARX SEC-3150 charging controller: $50,000
- ChargePoint Home Flex EV charger: $25,000
- Grizzl-E Smart 40A EV charging station: $20,000
Day Three:
- Alpine iLX-F511 multimedia receiver: $2,500 (bug collision bonus)
The pattern demonstrates that charging infrastructure represents a particularly vulnerable attack vector. Modern EV chargers function as networked IoT devices, often running complex software stacks with connectivity to home networks and cloud services. A compromised charger could serve as an entry point for lateral movement into home networks or potentially manipulate charging behavior in ways that create safety hazards.
Tesla Infotainment System Compromised
Synacktiv Team earned $35,000 by chaining two vulnerabilities to attack the Tesla Infotainment System through a USB-based attack vector. The exploit combined an out-of-bounds write flaw with an information leak, demonstrating how multiple moderate-severity issues can be weaponized into a high-impact attack chain.
USB-based attacks against automotive systems present a practical concern. While the attack requires physical access or social engineering to insert a malicious USB device, the infotainment system's role as the central hub for navigation, media, and vehicle controls makes it a high-value target. Successful exploitation could potentially access other vehicle systems through internal networks.
Industry Context and Escalating Rewards
The $1,047,000 payout reflects the growing value of automotive vulnerabilities on the exploit market. The trend shows consistent escalation:
- 2024: $1,323,750 for 49 zero-days (including two Tesla hacks)
- 2025: $886,250 for 49 zero-days
- 2026: $1,047,000 for 76 zero-days
The increased number of vulnerabilities discovered in 2026 (76 vs. 49 in previous years) suggests either improved research techniques, expanded attack surfaces in newer vehicles, or both. The competition's focus on automotive-specific targets rather than general software vulnerabilities means these findings directly impact vehicle safety and consumer protection.
Second-Day Surge
The competition's momentum built throughout the event, with Day Two particularly productive. Researchers demonstrated 29 zero-days on the second day alone, targeting a range of charging stations and controllers. This concentration suggests that charging infrastructure security remains inconsistent across manufacturers, despite the critical role these devices play in the EV ecosystem.
What This Means for Vehicle Owners
These findings have immediate implications for the rapidly growing EV market:
Charging Security: The prevalence of charger vulnerabilities indicates that home charging stations require the same security consideration as other networked devices. Consumers should prioritize chargers from manufacturers with established security practices and regular update mechanisms.
Infotainment Risks: While USB-based attacks require physical access, the infotainment system's connectivity to vehicle controls means any compromise could have broader consequences. Keep software updated and be cautious about unknown USB devices.
Vendor Response: The 90-day disclosure timeline means patches may be in development but not yet available. Vehicle owners should monitor manufacturer communications for security updates and apply them promptly when released.
The Economics of Bug Hunting
The prize distribution highlights the specialized knowledge required for automotive security research. Team DDOS earned $100,750 for second place, while Synactiv took $85,000 for third. These rewards reflect the complexity of automotive systems, which combine traditional software vulnerabilities with real-time operating systems, proprietary protocols, and safety-critical constraints.
The substantial payouts demonstrate that automotive security research has matured into a legitimate, lucrative specialization. As vehicles become more connected and autonomous, the value of these vulnerabilities—both to researchers and malicious actors—will likely continue increasing.
Looking Forward
Pwn2Own Automotive serves as a critical barometer for automotive cybersecurity health. The consistent discovery of high-severity vulnerabilities across multiple manufacturers and device types suggests the industry still has work to do in implementing secure development practices for connected vehicle components.
The competition's results should prompt automotive manufacturers to:
- Implement more rigorous security testing for charging infrastructure
- Establish secure update mechanisms for all connected components
- Consider the security implications of USB connectivity and physical access
- Invest in coordinated vulnerability disclosure programs
For security researchers, Pwn2Own Automotive 2026 confirms that automotive systems remain fertile ground for vulnerability discovery, offering both substantial financial rewards and the opportunity to improve vehicle safety for millions of drivers.

Comments
Please log in or register to join the discussion