Security
Vercel Implements Browser Verification for Enhanced Security
2/23/2026

Security
Mexico Forces Kill 'El Mencho' After US Help: Violence Hits Multiple States
2/23/2026
Security
Reddit Tightens API Access with New Authentication Requirements
2/23/2026

Security
French government database breach exposes 1.2 million bank account records
2/23/2026
Security
The Invisible Fracture in Unicode: When Security Meets Normalization
2/22/2026
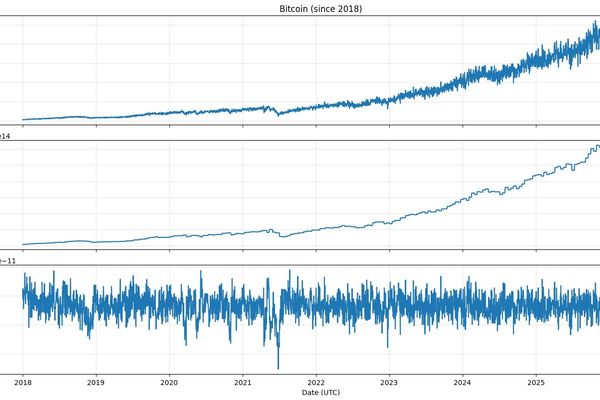
Security
Bitcoin Mining: The Delicate Balance Between Hash Rate and Difficulty
2/22/2026

Security
Generative AI Facilitates Global FortiGate Firewall Breach Campaign
2/22/2026

Security
Mar-a-Lago Security Incident Highlights Cost and Complexity of Protecting High-Risk Political Sites
2/22/2026
Security
Volatility Foundation Releases Complete Rewrite of Memory Forensics Framework
2/22/2026
Security
Holo Routing Project Advances Protocol Security with v0.9.0 Release
2/22/2026

Security
New START Expiration Unshackles Nuclear Arsenals, Accelerates Asian Arms Race Dynamics
2/22/2026
Security
Unicode Security Mechanisms: Safeguarding Identifiers in a Global Character Set
2/22/2026
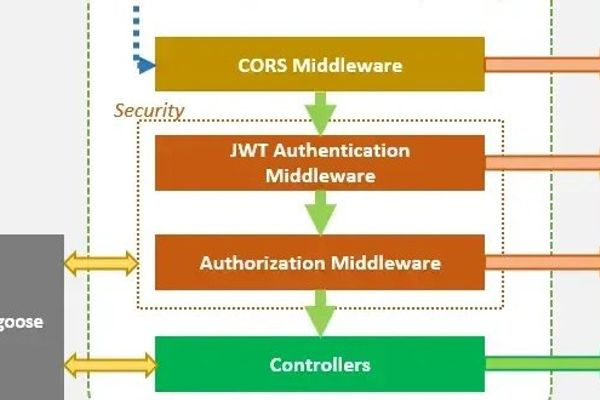
Security
Building a Production-Ready Authentication System with Express.js and MongoDB
2/22/2026