Okta warns of active voice phishing attacks using custom adversary-in-the-middle kits that bypass MFA by synchronizing with live calls, enabling data theft from enterprise cloud platforms.

Security teams at organizations using Okta's single sign-on (SSO) services face a new wave of highly coordinated attacks exploiting voice-based social engineering. According to an Okta Threat Intelligence report published this week, attackers are using custom phishing kits designed specifically for real-time voice interactions to bypass multi-factor authentication (MFA) protections and steal corporate data. These attacks represent a significant evolution beyond traditional credential harvesting.
The Anatomy of Voice-Enabled Phishing Kits
These adversary-in-the-middle (AitM) platforms operate as a service model sold to hacking groups targeting identity providers including Okta, Microsoft, and Google. Unlike static phishing pages, these kits enable live manipulation during voice calls:
- Real-time synchronization: Attackers control authentication flows through command scripts, modifying phishing page elements during calls based on victim actions
- MFA bypass: When services prompt for push notifications or one-time codes, attackers instantly update the phishing page to mirror legitimate prompts
- Credential relaying: Stolen credentials transmit directly to attackers via Telegram channels during calls
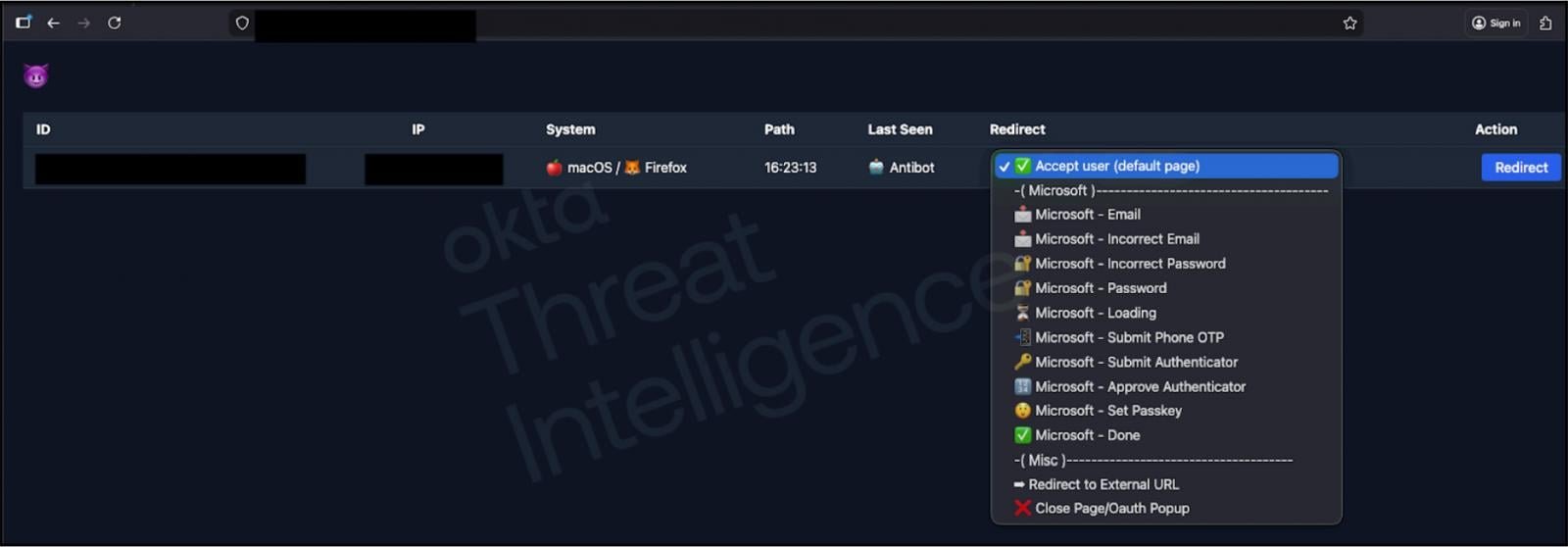 Caption: A C2 panel allowing real-time control of authentication flows (Source: Okta)
Caption: A C2 panel allowing real-time control of authentication flows (Source: Okta)
Attack Sequence and Impact
Threat actors conduct extensive reconnaissance before launching attacks:
- Identify target employees and their application access
- Spoof corporate IT numbers using VoIP services
- Convince victims to visit domains mimicking internal portals (e.g.,
company-internal[.]com) - Capture credentials and TOTP codes via synchronized phishing pages
- Access Okta dashboards to map available services
Once inside, attackers target data-rich platforms like Salesforce, Google Workspace, and Microsoft 365. As one threat actor's message to victims stated: "We looked through various apps on the employee's Okta dashboard... mainly exfiltrated from Salesforce due to how easy it is."
Why Okta SSO is a Prime Target
As the central authentication gateway for enterprises, Okta SSO provides access to:
- Cloud storage (Box, Dropbox)
- Collaboration tools (Slack, Zoom)
- CRM platforms (Salesforce)
- Development environments (Jira, Confluence)
- Financial systems (Coupa)
This centralized access makes compromised credentials exceptionally valuable. Evidence suggests threat actors affiliated with the ShinyHunters extortion group are actively targeting financial, fintech, and advisory sectors.
Practical Defense Recommendations
Okta emphasizes migrating to phishing-resistant authentication methods:
- Implement FIDO2 security keys or passkeys for cryptographic verification
- Deploy Okta FastPass for device-bound authentication
- Train employees using realistic vishing simulations
- Monitor SSO logs for unusual access patterns
- Implement number matching for MFA push notifications
As Okta stated: "It's crucial that companies take all necessary measures to secure their systems and continue to educate employees." Additional guidance is available in their social engineering defense blog.
Security teams should prioritize reducing MFA fatigue vulnerabilities and segmenting sensitive data access, as these attacks demonstrate sophisticated bypasses of traditional security layers through human manipulation.

Comments
Please log in or register to join the discussion