
Security
Microsoft testing Windows 11 batch file security improvements
2/27/2026

Security
Europol-led crackdown on The Com hackers leads to 30 arrests
2/27/2026

Security
Microsoft Opens Direct Dialogue on AI Security at RSA Conference
2/27/2026

Security
NATO Approves iPhone and iPad for Classified Information Handling
2/27/2026
Security
Cloudflare's Security Verification System: Protecting Websites from Bot Attacks
2/27/2026
Security
NetBSD Jails: Bringing Container-Like Isolation to the BSD Ecosystem
2/27/2026
Security
Reddit Blocks Automated Access, Sparks Developer Frustration
2/27/2026

Security
Trojanized Gaming Tools Spread Java-Based RAT via Browser and Chat Platforms
2/27/2026
Security
Cloudflare Security Check: What This Verification Page Means for Your Browsing Experience
2/27/2026
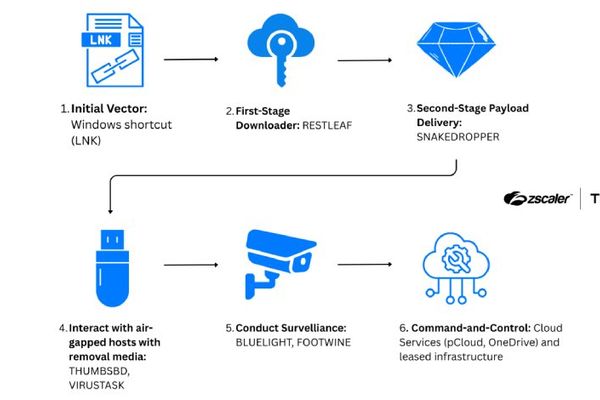
Security
ScarCruft's New Arsenal: Zoho WorkDrive Backdoor and USB Malware Target Air-Gapped Networks
2/27/2026

Security
European DIY Chain ManoMano Data Breach Impacts 38 Million Customers
2/27/2026

Security
Dutch Police Back Odido's No-Ransom Stance as ShinyHunters Escalate Data Leaks
2/27/2026
Security
Cloudflare Security Verification Intercepts Axios Access
2/27/2026